Abstract: The attack on Tower 22—an outpost in Jordan used by the U.S. military—that killed three U.S. service members was an important reminder about the threat posed by stand-off weapons, especially armed one-way-attack drones. While few details have been publicly released about the location from which the hostile drone was launched, the U.S. military’s response points to the drone having been operated by a nearby Iranian proxy. Over the past several years, this type of threat—the targeting of U.S. military facilities in Iraq and Syria by shorter-range stand-off weapons—has become common. But there have also been signs of a broader threat that has emerged, the threat of long-range stand-off terrorism. This article conceptualizes, and attempts to define, this emerging threat vector. It also traces signs of its emergence and initial evolution, and discusses implications associated with this coming, on-the-horizon problem. Recent long-range drone and missile attacks attributed to the Houthis, a capability that Iran has helped to strategically shape, highlight how the Houthis are both a first mover and a leading-edge indicator of the threat. While adoption will likely be limited and constrain the scope of the threat, at least initially, long-range stand-off terrorism will be attractive to some extremists because it opens-up new attack pathways, can enable surprise, and has the potential to deliver a potent psychological, ‘we can strike you from afar’ punch. Over the next decade advancements in commercial technologies and systems will also make range, and extended range, more accessible for violent non-state-entities, making it likely that in the future long-range terrorism will become more of a threat.
In August 2003, in what was an important breakthrough in remote-control aviation, Maynard Hill—“a pioneer in unmanned and model aircraft”1—successfully flew a radio-controlled model airplane he built from commercial parts nearly 1,900 miles across the Atlantic Ocean, from Newfoundland to the coast of Ireland. The six-foot balsa-and-Mylar plane that made the transatlantic flight weighed 11 pounds and utilized less than a gallon of gas.2 The flight “set records for distance in a straight line … and flight duration: 38 hours, 52 minutes, 14 seconds.”3 It was an incredible and enterprising achievement for a private citizen.
Despite having occurred more than 20 years ago, the flight is still immensely relevant today, particularly when considering its implications for terrorism. Not only does Hill’s feat demonstrate that such a long-range flight is possible, highlighting a capability that could be mirrored by other individuals or non-state teams, it also provides a window into a not-so-distant future when non-state actors will be able to deploy systems to conduct attacks, and other operations, from large stand-off distances or what might have previously been considered unfathomable ranges, like a flight across the Atlantic Ocean. Enabled by Iran, the Houthi movement’s reported ability to conduct missile and drone attacks against Saudi Arabia and the United Arab Emirates and more recently Israel,4 from great distances, including those that exceed 1,000 km, highlights how the era of long-range stand-off terrorism has already—in part—emerged.
This articlea conceptualizes and gives definition and form to this new strand of terrorism, a type of terrorism that while already visible still holds much room for growth and evolution. The article first provides a general overview of the attractiveness of stand-off weapons, and the concept of long-range stand-off terrorism. The second part of the article explores factors that shape terrorist interest in and adoption of new technologies and approaches and discusses how long-range stand-off terrorism is emerging as a new threat vector. The article’s third section highlights key accelerants and limiting factors that will likely shape the timeline of long-range stand-off terrorism and its potential proliferation as a threat and capability area. Section four highlights several real-world examples that provide insight into how range, and the extension of range, is a capability area that state, non-state, and proxy actors are actively pursuing and, in some cases, have already operationalized. The article concludes with a review of key implications.
Terrorism and the Concept of Long-Range Stand-Off Attacks
Stand-off weapons, or weapons that can be used to attack adversaries from a distance, have been embraced by terrorists, and are not new.5 This is because these types of weapons provide the same types of benefits to violent non-state actors as they do to states: They reduce force attrition and make it harder for the targeted party to identify the source of the attack and respond quickly.b Hamas’ brutal attack on October 7, 2023, for example, involved the integrated use of many different types of weapons, including direct contact weapons, such as small arms and bladed weapons that allowed Palestinian militants to attack Israeli civilians in close and more intimate ways, and stand-off weapons, typified by rockets and drones, that allowed the group to attack—and repeat those attacks—from a longer stand-off distance. Terrorists have also sought out and attempted to conduct attacks utilizing surface-to-air missiles, another type of stand-off weapon. For example, in November 2002, two surface-to-air missiles were fired at an Israeli charter Boeing 757 airplane after it took off from Mombasa, Kenya. Fortunately, the missiles missed the aircraft, which was carrying 260 passengers.6
Long-range stand-off weapons, as the name denotes, are weapons that can be deployed a greater distance away from the intended target(s). There does not appear to be a lot of agreement, however, about what constitutes a “long-range” weapon system generally. This is because different frameworks are used to classify range in relation to the type of system or platform. For example, a short-range ballistic missile is often categorized as having a range of between 300-1,000 km, while medium-range, intermediate-range, and intercontinental ballistic missiles are usually viewed as, respectively, having the following ranges: 1,000-3,000 km, 3,000-5,500 km, and more than 5,500 km.7 Cruise missiles, alternatively, are often categorized by their purpose or modality, such as whether they are used to target ships, conduct land attacks, or carry nuclear payloads.8 The U.S. Department of Defense uses a separate framework to classify unmanned aircraft systems (UAS). That framework breaks UAS into five different group categories, with those groups primarily being organized by UAS weight, operating altitude, and flight endurance.9 NATO’s UAS classification scheme has three UAS classes instead of five.10 Other frameworks developed by researchers, industry, and drone enthusiasts also exist online. One such framework proposes a guide that breaks down UAS by five range limits: very-close range (5 km), close-range (50 km), short-range (150 km), mid-range (644 km), and long-range (more than 644 km).c
An initial, proposed way to define what constitutes long-range stand-off terrorism is to build off this latter range framework, and for it to include three key components: 1) the deployment of an unmanned weapon or system by 2) an individual, non-state group, or network from a stand-off distance greater than 800 km (nearly 500 miles) from its intended target(s) to 3) conduct a terror attack—or other type of operation to advance a terror movement’s agenda. It should be stressed that the proposed 800 km range threshold is an initial marker that is being shared to provoke debate and conversation among stakeholders about what the ‘right’ or most appropriate range threshold for a long-distance stand-off terror attack should be. In using this type of range threshold, long-range stand-off terror attacks could include, for instance, the deployment of an armed UAV, cruise missile, or another type of delivery vehicle, across an ocean, from one region of the world to another region, across multiple countries, from one country to another, or over a large distance within a country.
This type or modality of attack is different from other methods, such as remotely inspired attacks, that enable terror networks to conduct attacks in countries located a far distance from the operation’s principal planners and/or controller. In those types of attacks, the violent non-state actor inspires, provides support to, or helps guide a human operative or team of operatives located in (or who can gain access to) a separate country where the attack takes place. This method has allowed groups such as the Islamic State to achieve long-range attack capability without having to go through the hassle, and associated risk, of inserting an operative, or team of operatives, in a foreign country located far away.d The core difference between long-range stand-off attacks and those that are remotely inspired is that the former involve incidents where the weapon is delivered by a machine that has been programmed and launched (or is being controlled) by an actor from afar—a great distance away from the target—rather than where a human, armed with a weapon, serves as the direct agent of violence.e
Preferences, Tradeoffs, and Long-Range Stand-Off Terrorism as an Emerging Threat Vector
Like other players, terrorists and extremists need to navigate tradeoffs and explore the costs and benefits of experimenting with and adopting new technologies and systems. This is because adopting new or novel weapons, systems, and capabilities have the potential to amplify existing risks and introduce new ones. As part of its calculus, a group, network, or individual must also examine whether the deployment or utilization of a new technology or approach will advance their specific goals and whether they have the resources, knowledge, and know-how to utilize the new addition in an effective way. These and other reasons help to explain why most extremist and terrorist entities usually prioritize and prefer more ‘tried and true’ or reliable weapons and methods, such as the use of the gun and/or a bomb in attacks.11 f
Over the course of time, that has been an enduring feature of terrorism. But there have always been important exceptions and outliers, first movers and innovators that have been bolder and more risk accepting in terms of how they approach, experiment with, and adopt new technologies and weapons. The access that violent non-state actors have to advanced commercial technologies and systems, and technical know-how (which is often widely shared) has been disrupting how extremists and terrorists innovate and the capabilities that are now within their reach.
The Islamic State’s successful and effective weaponization of drones, and the group’s ability to scale that threat, is an important example in this regard. Through some creative and simple tinkering, the group was able to transform commercial quadcopters into affordable, small, and viable bomb-dropping weapons of war, which for a period were a nasty and effective nuisance. In doing so, the Islamic State’s breakthrough drone innovation demonstrated what was possible, paving the way for other actors to follow, further develop, and push this new aerial capability in new directions. Today, terror drone usage and terror drone weaponization is more diffused and common, and future historians will likely give due credit to the important role the Islamic State played in helping to shift the terror drone threat from a more novel, niche threat to a more ubiquitous one.
The arc of terror drone weaponization and its diffusion is a useful parallel to situate the threat of long-range stand-off terrorism today. More than 15 years ago, in 2005 and 2008, the Institute for Defense Analyses (IDA) and RAND, respectively, released two key reports that explored the idea and threat posed by future terrorist use of UAVs and cruise missiles to conduct attacks at stand-off ranges.12 The RAND report concluded in 2008 that UAVs and cruise missiles were a novel and “niche threat”—“potentially making some contribution to the overall asymmetric and terrorist threat, rather than being an attack mode likely to be widely embraced by such actors.”13 That finding, and way of characterizing the threat, generally holds true today. If the Houthi case is set aside, the modality remains boutique and niche. But the Houthis’ long-range missile and drone attacks—particularly those against specific civilian or mixed-use infrastructure such as airports, which there is a stronger rationale to view or consider as being acts of terrorism—challenge this characterization.g As will be outlined below, attempts attributed to the Houthis to strike Eilat in southern Israel challenge it as well. While long-range stand-off Houthi attacks have largely been focused on striking military targets and national infrastructure, such as Saudi Aramco facilities, the Houthis cross-border aerial warfare campaign has been just that—a multi-year campaign during which long-range stand-off attacks have become a steadier and more regular, and not niche, attack feature.
This is troubling because advancements in commercial technologies and systems are helping to make range, and extended range, more accessible generally, making it likely that over the coming decade more violent non-state actors will engage in longer and longer-range stand-off attacks.h In that sense, the Houthis’ long-range stand-off attacks are just an early manifestation, or leading-edge indicator, of a broader, coming problem. Thus, while long-range stand-off terror attacks remain niche for non-Houthi groups at the moment,i over time it seems likely, and arguably quite probable, that they could evolve into a more common threat feature for categories of violent non-state actors.
Accelerants and Limitations: Factors Shaping Long-Range Stand-Off Terrorism and Future Adoption
Several key factors will shape the timeline associated with long-range stand-off terrorism and its future adoption. At a high-level, these factors can be framed as accelerants (dynamics that are helping to enable the emergence of long-range stand-off terrorism) and limitations that work to slow and constrain violent non-state actor adoption of this operational modality.
One key accelerant, as Hill’s transatlantic flight demonstrated more than two decades ago, is that commercial technologies and systems can be leveraged to execute long-range missions. The capability exists and has been proven. But the power and potency of this accelerant is itself constrained, as just because the capability has been demonstrated does not mean that mirroring Hill’s flight would be an easy thing for a violent non-state actor to do. A lookalike of Hill’s long-distance flight—reimagined for terror purposes—for example, would require the right know-how and technical expertise, and access to and creative use of key commercial equipment and components. Hill and the team that supported him were seasoned experts, and they worked together to overcome technical challenges14 that any other non-state team would face. Terrorist actors would likely face significant additional challenges including air defense as well as drone detection and countermeasure systems.
Some of the core issues and challenges that a non-state team would need to navigate to extend UAS range include the size, weight, and design of the drone; propulsion and power; control, navigation, and communication; and environmental factors (e.g., wind and weather).16 Further, if a terror entity wanted to use a long-range stand-off weapon, such as an armed UAS, some of these challenges (e.g., weight) would be compounded and involve system tradeoffs (e.g., a UAS with a longer range, but with a more limited explosive payload to make the UAS lighter). The system’s ability to avoid detection and mitigate any defensive UAS countermeasures would also be a key consideration. Precision would be an issue as well, especially if the actor wanted to strike a moving/non-fixed target. These obstacles would likely deter all but the most committed and boldest of actors—limiting the scale of the threat, at least initially.
A second accelerant is ongoing advancements made to commercially accessible technologies that could be leveraged to conduct a long-range stand-off terror attack. Today’s commercially available drones, for example, are more efficient, more capable, and can fly farther, faster, longer, and with heavier payloads than drones that were available to consumers a decade ago. Stepwise and more radical advancements in consumer UAS will continue to elongate range and make longer-range UAS attack pathways more viable for violent non-state actors. The predominance of commercial UAS that are available today are powered by lithium-ion batteries, which constrain how far and for how long those drones can fly. But alternative powering options, such as UAS powered by hydrogen fuel cell technology or hybrid fuel/powering systems (i.e., solar), are already commercially available. In 2022, for example, the South Korean company Doosan won the CESj Best Innovation Award for its DS30W—the “world’s first mass manufactured hydrogen fuel cell drone.”17 Honeywell and other companies produce and sell hydrogen fuel cell drones as well.18 UAS powered by hydrogen fuel cell technology are attractive because they are “smaller, lighter, more versatile and more resilient than alternatives like batteries or small gasoline and diesel engines,” offering what is claimed to be “three times the range of flight time of lithium battery powered drones.”19 The H2D250, a hydrogen powered UAS made by Heven Drones, for instance, reportedly has an eight-hour flight endurance and has a 10 kg payload capacity.20 Over the coming decade, hydrogen fuel cell and solar UAS technology will evolve and mature, and will also likely become more available and accessible to the average consumer, which will make longer ranges more accessible as well. Other disruptive technologies, such as generative artificial intelligence, will also mature and will likely be used by extremists to help them optimize system performance and to overcome, or devise creative solutions to, technical long-range UAS challenges.
A third accelerant that is likely to make long-range stand-off terrorism an attractive option for select categories of terrorists is the benefits the attack modality offers. At a strategic level, two important advantages stand out. The first is surprise: For the first movers and lead innovators, long-range stand-off attacks will likely be unexpected, allowing the group, network, or individual to surprise and likely shock its enemy. Surprise may be fairly easy for these first movers to achieve, as if these types of long-range attacks have not happened before, as they have already in the Middle East, terrorists will likely have a broad attack surface area with many undefended and vulnerable targets from which to choose. The second strategic benefit and point of attraction is the symbolic power of being able to conduct such an attack. Symbolism is especially relevant for terror groups, proxies, and states that have been targeted by armed drones. The deaths of Qassem Soleimani (the former leader of the Islamic Revolutionary Guard Corps’ Quds Force) and Abu Mahdi al-Muhandis (the commander of the Iranian proxy Kata’ib Hezbollah) who were both killed in a January 2020 U.S. drone strike are an important case in point. If Iran, or an Iranian proxy, were able to conduct a long-range stand-off assassination of a key U.S. figure using an armed drone, the operation would be a powerful and symbolic form of revenge. The significance of Iran using a similar type of weapon to assassinate a high-profile U.S. person, or partner, would not be lost on the world. Such an attack would also carry another important psychological message: ‘You—the United States—are not as secure as you think you are, and we have the ability to strike you from afar.’
There are related operational and tactical benefits to long-range stand-off terror attacks. The 2008 RAND study discussed earlier identified five key benefits, or adversary operational problems, that UAVs and cruise missiles can solve. These included enabling 1) attacks over perimeter defenses, 2) attacks over national borders, 3) multiple simultaneous attacks, 4) attack campaigns, and 5) aerial attack of area targets with unconventional weapons (i.e., WMD terrorism, especially chemical and biological attacks).21
Just because these accelerants and benefits exist does not mean that terrorist groups will broadly seek out and/or adopt long-range stand-off terrorism as an attack modality. The approach, given the technical hurdles involved when weighed against the ease of use associated with other methods or weapons, will only appeal to those types of extremist networks that have an interest in attacking targets from a long range, and that believe such an attack would advance their specific cause and/or goals. Terror networks that are more concerned with local issues, for example, would likely not want to expend the resources or take on added risk to experiment with and develop the capability. But terror networks, or regimes, that have more resources, that have key enemies located a great distance away, and/or that embrace a ‘far-enemy’ targeting mindset would likely be more interested in long-range stand-off terrorism. Given that resources will be a key determining factor for first movers, it is not surprising that the initial instances of long-range stand-off terrorism have been tied to the Houthis—a state-supported entity.
Yet, as range becomes increasingly accessible to violent non-state actors, it is also possible that the emergence of long-range stand-off terrorism could empower other types of existing actors or lead to the creation of new ‘players.’
Current Threats and the Stretching of Range
Concern about non-state groups—including terrorists—utilizing UAS to conduct long range stand-off terror attacks is not new. For example, in 2017, Owen West, who was then serving as the Assistant Secretary of Defense for Special Operations and Low Intensity Conflict (ASD SO/LIC), warned that “in about five years”22 that “non-government groups would be able to acquire and weaponize drones which could cross the Atlantic.”23 When asked, also in 2017, whether “the commercial market is really headed toward building small drones that might fly thousands of miles across the unforgiving open air of an ocean,” Matt Scassero, the director of the University of Maryland’s UAV test site, stated: “the short answer is yes.” In his view, “the technology will be there to support that kind of flight operations … Long-range drones will be able to fly across oceans within a fairly short amount of time, possibly five years.”24 So, the future during which terror actors who possess the intent and interest in conducting a long-range stand-off attack might be here sooner than most expect. If the predictions of individuals like West hold true, we should already be at, or approaching that, moment.k There is also a strong case to be made that the threshold has already been crossed by the Houthis some time ago.
News reports and information about key conflicts provides plenty of evidence about how state and non-state actors continue to extend the range from which they can attack. One of the most relevant examples, as discussed above, is the long-range drone and cruise and ballistic missile attacks conducted by the Houthis. According to data compiled by ACLED, between “2015 and 2 April 2022, the Houthis engaged in nearly 1,000 rocket/missile attacks and over 350 distinct drone attacks.”25 Attacks against Saudi Arabia were a steady feature of the Houthis cross-border aerial warfare over that period, but in 2018 there was a noticeable shift in the capability and range of Houthi missiles and drones, and an expansion of targets.26 For example, in 2018, “the Houthis claimed to have struck Dubai airport more than 1200 km away with a new long-range drone called Samad-3. They also claimed to have attacked Riyadh airport.”27 At the time, there was some skepticism about the Houthis’ claims about the range of its Samad-3 UAS variant. But as David Hambling reported:
In early 2019 a UN panel examined four examples of a new type of drone recovered by Saudi forces. Smaller than a light aircraft, it had a wingspan of 4.5 meters and unlike other Houthi drones, it was built from parts sourced internationally. The rear-mounted engines were either German-made 3W110i B2 or a Chinese DLE 170s bought on the open market. Some examples were equipped for reconnaissance, others were on one-way missions as cruise missiles, with a forty-pound payload of explosives mixed with ball bearings. The UN panel assessed the speed of the new drone at 200-250 km/h and maximum range of 1500 km. What was clear was that the long-range Samad-3 was real.28
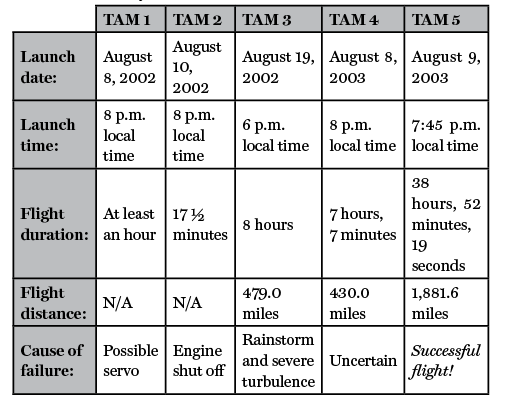
A report released this month by the Defense Intelligence Agency (DIA) spotlighted the same general range conclusion, and provided additional evidence about how the Houthis continue to extend the range of their UAS and missiles due to help provided by Iran. The DIA report, for example, included two regional maps with range rings: one for UAS systems utilized by the Houthis and another for missiles. DIA estimated the range of the following key Iranian / Houthi UAS: Shahed 131 (Waid 1) – 900 km, Sammad – 1,800, and Shahed 136 (Waid 2) – 2,500 km.29 l
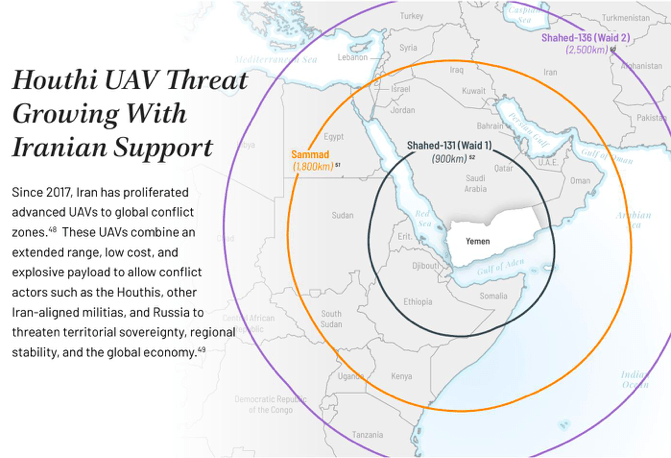
The DIA report highlighted eight different missiles. The three missiles with the longest range included: Qiam/Rezvan (Burkan-3) ballistic missile – 1,200 km, Shahab-3 (Toofan) ballistic missile – 1,950 km, and Project 351/Paveh (Quds-4) land-attack cruise missile – 2,000 km.30 m
Drone and ballistic and cruise missile attacks attributed to the Houthis over the past two years demonstrate the long-range threat, and how the movement’s capabilities are far from being just a theoretical problem. It is a serious one. Two examples bring the issue into focus. First, on January 17, 2022, the Houthis claimed to have conducted an attack in Abu Dhabi utilizing explosive-laden drones and ballistic missiles that struck a key state-owned oil facility, which killed three civilians, and that caused a fire at Abu Dhabi’s international airport.31 The U.S. government and United Nations both classified that attack as an act of terrorism.32 A week later the Houthis reportedly launched more ballistic missiles at the UAE. In response to that attempt, “U.S. forces at Al Dhafra Air Base, near Abu Dhabi… [shot down] two inbound missile threats with multiple Patriot interceptors.”33 It is believed that the Houthis launched the missiles for the second attack from a site in Yemen’s al-Jawf province, a distance of “around 1,350 kilometers (840 miles) southwest of Abu Dhabi.”34
Second, since the October 7 terrorist attack in Israel the Houthis have repeatedly attacked and attempted to attack military and commercial vessels35 n in the Red Sea and Gulf of Aden. Another component of the Houthi response has been efforts to strike Israel with ballistic missiles directly. On October 31, 2023, for example, the Houthis reportedly fired a medium-range ballistic missile at southern Israel, believed to be intended for the city of Eilat, located over 1,000 miles (1,600 km) away from western Yemen.o That attempt was a ‘first’ and broke barriers in three ways. The first barrier was distance, as according to reporting by Popular Mechanics, “the Houthi missile traveled 1,000 miles, making it… the longest range ballistic missile attack ever.”36 The second barrier the Houthi attempt broke was that the “Houthi missile warhead was technically in space when it was destroyed, making it the first hostile action to take place off-planet.”37 In other words, as two Israeli officials told The Economist, this was the “first ever combat interception in space.”38 The third barrier, or ‘first’, that the event triggered lay in how Israel responded to the in-bound threat. The Israeli Defense Forces (IDF) intercepted the Houthi missile above the Negev desert using the Arrow-3 component of its air defense system.39 Israel’s use of its Arrow-3 capability to intercept the Houthi missile is noteworthy because the Arrow system, which is comprised of Arrow 2 and Arrow 3 components,40 is the “top tier of Israel’s multi-layered integrated air defenses.”41 While Arrow 2 is focused on defense on regional and medium range threats, which are concerning in their own right, Arrow 3 is an “exo-atmospheric missile capable of long-range interception by traveling through the lowest layer of space during its flight path.”42 Israel’s successful Arrow-3 intercept of the ballistic missile fired by the Houthis in late October 2023 was “the first operational success since the weapon entered service in 2017.”43 That initial long-range Houthi attempt to strike Israel was not a one-off or one-time capability, however, as in early February 2024, the Houthis tried again. The IDF also intercepted that missile, marking the second successful operational Arrow-3 intercept.44 And on February 22, 2024, the Israelis intercepted yet another Houthi attempt.45
The Houthi’s long-range capabilities are a concern as a stand-alone threat, but they raise other concerning questions about proliferation and additional terror threats as well. For example, recent reports from the United Nations Monitoring Team have suggested that the Houthis have been providing al-Qa`ida in the Arabian Peninsula (AQAP) with drones46 and components,47 and with operational training in how to use them.48 If these reports are true, they elevate concerns about proliferation and the extended chain of proliferation.
It is well known that Iran provides support and weapons to the Houthis, and that the development of Houthi UAS and missile capabilities has been strategically enabled by Iranian platforms, designs, technology, training, and advice. For example, when asked in a 60 Minutes interview aired in mid-February 2024 whether the Houthis could be engaging in its campaign of attacks in the Red Sea without Iranian support, the Deputy Commander to U.S. Central Command, Vice Admiral Brad Cooper, responded: “No. For a decade the Iranians have been supplying the Houthis, they have been resupplying them … they are advising them, and they are providing targeting information. This is crystal clear.”49 He went on to add: “The Islamic Revolutionary Guard Corps [IRGC] is inside Yemen and they are serving side-by-side with the Houthis … advising them and providing targeting information.”50
Prior analysis of ‘long-range’ drone and missile attacks claimed by the Houthis also indicates that there might be ‘more than meets the eye’ about Houthi capabilities and the entities responsible. For example, in 2020 an independent panel of U.N. experts concluded “that, despite their claims to the contrary, the Houthi forces did not launch the attacks on Abqaiq and Khureys [Saudi Arabia] on 14 September 2019.”51 At the time, the investigators doubted “the uncrewed aerial vehicles and land attack cruise missiles used in that attack had a sufficient range to have been launched from Yemeni territory under the control of the Houthis.”52 They were also concerned about evidence that the targeted facilities in “Abqaiq and Khurais were approached respectively from a north/northwestern and north/northeastern direction, rather than from the south, as one would expect in the case of a launch from Yemeni territory.”53 Months prior, in May 2019, there was another drone attack against oil facilities in Saudi Arabia. The Houthis claimed responsibility for that incident as well,54 but it appears that the drones actually came from Iraq.55 As Michael Knights astutely noted in 2021, after the 2019 attacks, “Iran and its proxies now seem more adept at controlling the narrative about where these strikes originate…”56
There are still questions about whether the same approach and strategy to deflect or mask attribution has been used in more recent attacks. For example, as The Economist noted in November 2023, it “remains unclear whether the Houthis or their Iranian patrons launched the October 31st [ballistic missile] attack” that targeted Israel.57 But, as also highlighted by The Economist, that “is part of the appeal” because then “Iran’s revolutionary guards can blame strikes on Houthi militants.”58 These dynamics highlight how there is a need for care and caution in how Houthi capabilities are described and just how quickly and authoritatively long-range attacks should be attributed to the movement.
Analysis of recovered Houthi UAS by Conflict Armament Research (CAR) provides additional insight into the Houthi-Iran system and capability overlap.59 In 2017, for example, “evidence documented by CAR … suggests that the Qasef-1 UAV is not of indigenous design and construction, but is Iranian-manufactured and has been supplied in batch to Houthi and Saleh-aligned forces in Yemen.”60 Another CAR publication released in 2020 analyzed a Sammad-pattern UAV recovered by UAE forces, and CAR found that “several of the components” of the Sammad drone “resemble those of the Qasef-1, but with a few notable differences.”61
Iran’s sharing of its technology and systems is much broader problem. As noted by The Economist:
Over the past 20 years Iran has supplied drones, rockets and missiles, as well as the know-how to make them, to Hamas in Gaza, the Houthis in Yemen, sundry militia in Iraq and Syria and, most notably, Hizbullah in Lebanon. In 2007 Hamas had several hundred rockets, according to Israeli estimates. That jumped to 10,000 in 2014 and then tripled to 30,000 in 2021. Hizbullah’s more sophisticated arsenal went from around 15,000 missiles in 2006, the year it fought a war with Israel, to some 150,000 today. Around 400 of those are long-range missiles which can hit anywhere in Israel.62
Not only has this activity from Iran been “changing the military landscape of the Middle East,”63 it has also been shaping conflicts much further afield. Initial CAR analysis of Shahed drones employed by Russia in Ukraine in 2022, for example, found that “they were in fact all Iranian-made Shahed-131 and Shahed-136 UAVs.”p CAR’s study of Russian Shahed drones in Ukraine has also highlighted the importance and centrality of commercial components to the Shahed platform. According to CAR, “more than 70 manufacturers based in 13 countries and territories produced” the components they found, “with 82 per cent of them manufactured by companies based in the United States.”64
A tactic and capability that Iran recently claimed heightens the concern about what other systems and know-how Iran might be sharing, as it demonstrates that there are creative ways to ‘shrink’ range and make longer range strikes possible and to conceal or disguise those attempts. In February 2024, for instance, Iran’s Revolutionary Guard Corps (IRGC) released a video that highlighted how it “fired two ballistic missiles from launchers disguised as standard shipping containers that were hosted aboard one of its sea base-like vessels.”65 It will be interesting to see if this is a capability that is shared with the Houthis or other entities.
While the Houthi example provides a window into non-state actor capabilities, or that of a state-supported proxy, recent long-range UAS attacks conducted by the Ukrainian government highlight how states are devising ways to strike targets at longer and longer stand-off ranges as well (as one would expect). As Stacie Pettyjohn has noted, “over time, it has become clear that adapted commercial or homemade kamikaze drones played an increasingly important role and enabled Ukraine to hit targets deep inside Russia.”66 In mid-January 2024, Ukraine claimed to have used a domestically produced drone to strike targets in St. Petersburg, Russia, a distance of 1,250 km (close to 800 miles) away.67 In August 2023, Ukraine had reportedly used cardboard drones developed by an Australian company to attack an airfield in Russia’s Kursk Oblast.68 The airfield in Kursk was a closer target, but that attack reportedly “damaged a Mig-29 and four Su-30 fighter jets, two Pantsir anti-aircraft missile launchers, gun systems, and an S-300 air surface-to-air missile defence system.”69 Ukraine’s innovative and effective use of unmanned drone boats, including extended range ones, to conduct stand-off attacks against Russian ships highlights the multi-dimensional nature of the coming threat and its potential.q In that sense, as Marc Jacobsen has highlighted, Ukraine’s innovative use of drones and other unmanned systems provides a “window into the future of warfare.”70
Extremists recognize that the Ukraine conflict, and the drone-related innovations emerging from that conflict, provides that window. In 2023, a PhD student in the United Kingdom, Mohamad al Bared, was found guilty of a “terror offence after designing [a] ‘kamikaze’ drone for ISIS.”71 Russian drone attacks in Ukraine were a key inspiration for him. To develop his drone prototype, al Bared “copied the design of a Tomahawk missile and produced the wings on a 3D printer, sending weekly updates to ISIS, so they could be replicated.”72 The prototype was designed to deliver an explosive payload across an 8 km range.73
This Islamic State interest in such a prototype is not surprising, as the group has sought to enhance the capabilities of fixed-wing drones. For example, according to additional CAR analysis in 2020, the Islamic State “attempted to develop high-speed drones powered by pulse jet engines like those used in V-1 bombs dropped on the UK during World War Two.”74
These recent real-world examples showcase how different types of actors are seeking out ways to extend range and engage in stand-off attacks from afar. They also highlight how different types of actors, state and non-state alike, learn from and receive inspiration from one another.
Conclusion
Long-range stand-off terrorism is an on-the-horizon threat that lurks. It is a threat vector that is already visible, and it is also a threat that will likely, over the next decade, become more of a menace as commercial technologies make range more and more accessible for non-state entities. While adoption will likely be limited and constrain the scope of the threat, at least initially, long-range stand-off terrorism will be attractive to some extremists because it opens up new attack pathways, can enable surprise, and has the potential to deliver a potent psychological, ‘we can strike you from afar’ punch.
Now is the time to think about and advance efforts to prepare for the threat so it can be more proactively mitigated. One important issue that needs to be considered is the ‘art of the possible’ and what a non-state team can achieve utilizing commercial and other accessible technologies, components, and systems. Maynard Hill unwittingly planted an important capability marker in 2003. Since then, there have been other initiatives and efforts, such as Solar Impulse 2 and the Pacific Drone Challenge, that have sought to push the boundaries of what it is possible for non-state teams to achieve.75 If it is not doing so already, the United States should evaluate the pros and cons and consider sponsoring a competition for non-state teams to replicate Maynard Hill’s flight using more advanced technologies as a way to further probe the feasibility of long-range commercial UAS flights. Since Iran’s Shahed 136 UAS boasts a range of 2,500 km, another similar idea would be for a government, or consortium of governments, to run an effort to test and identify the actual range of a recovered Shahed 136, a reconstructed one, or a newly constructed platform built to spec. Both approaches would provide useful data to better understand the current ‘art of the possible’ and how this threat vector is evolving—potentially minimizing the risk of surprise. These types of efforts would also highlight key technologies, components, and software that are critical to the extension of range, and that require care and potentially enhanced monitoring.
Indicators are another important issue to consider. Maynard Hill’s five TAM flights are instructive in this regard. As highlighted in Figure 1, Hill’s first four TAM attempts failed for various issues, ranging from power failure to weather and an uncertain reason. Those four failed flights serve as an important reminder about how failure is an integral part of the development of any new capability. Like Hill, violent non-state actor teams, will likely need to test and trial-run their system before engaging in a successful long-range stand-off operation. If not executed carefully, these trial run efforts will leave an observable signature. The United States and its partners should remain on the lookout for evidence and data points that speak to long-range terror intent and the development and deployment of a system capable of executing such a mission. This could include, for example, UAS that crash under mysterious circumstances in unexpected areas, especially those similar in design to known UAS of concern; attempts by specific actors or networks to acquire or field specific components; rumors about a terror network’s interest in such a weapon; evidence that speaks to the recruitment or placement of key technical experts; recovered plans or plots; and other types of indicators.
The availability of commercial systems and components, and the open-source character of the terror UAS threat, also means that partnerships will be key to mitigating the future scale, scope, and intensity of long-range stand-off terrorism. This would obviously include meaningful partnerships with industry and key companies that produce and/or sell or distribute specific systems, hardware, software, and components that could be exploited by non-state teams, and that could be used by governments to detect, defeat, and/or counter those efforts. Weapons-tracking experts—individuals and organizations, such as CAR, that document and investigate components and systems used by militaries and non-state armed groups on the frontlines of key conflict zones—and experienced hobbyists are two other key groups where bolstered partnerships should be explored and ideally pursued. These types of partnerships will enable governments to learn more about the problem and how it is evolving, which will allow states to better anticipate and proactively mitigate future long-range stand-off threats, including those motivated by terrorism.
The architecture to detect and counter long-range threats, to include those from small, unmanned platforms, is another obvious area that deserves additional consideration. Today, compared to a decade ago, there is a copious and diverse number of counter-UAS options that are available, and that are more capable. But the campaign of drone, missile, and rocket attacks against closer U.S. targets in Iraq and Syria by Iranian supported groups after Hamas’ October 7 attack,76 to include the January 2024 one-way drone attack against Tower 22 in Jordan, which resulted in the death of three U.S. service members, highlights how localized air defense gaps and seams still exist—even for closer-to-the-frontline military outposts that knew such attacks were likely.
Substantive Notes
[a] Editor’s Note: This article is the first in a new recurring series in CTC Sentinel entitled “On the Horizon” that will examine emerging counterterrorism challenges.
Citations
[1] Sarah Brown, “Model Airplane Legend Maynard Hill Dies at 85,” AOPA, June 10, 2011.
 Eurasia Press & News
Eurasia Press & News



