Months after government servers were hit by sophisticated cyber-attacks, questions remain over Montenegro’s readiness to confront the next inevitable assault, experts say.
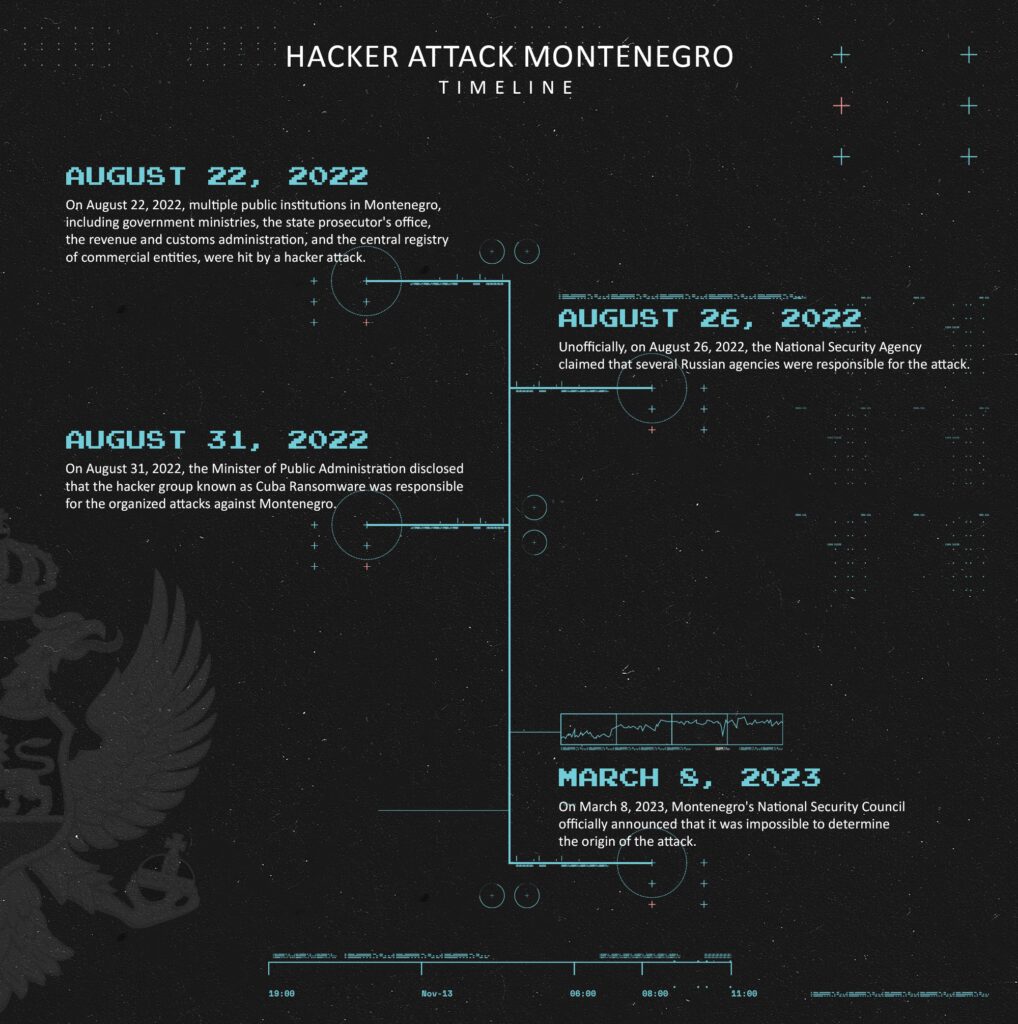
First they blamed Russia, then a gang called Cuba Ransomware. Months later, authorities in Montenegro still have no definitive answer as to who was behind “unprecedented” cyber-attacks in August last year targeting a host of government services.
Whatever the answer, experts say Montenegro remains just as vulnerable to such attacks, citing a shortage of talent and a lack of investment in cybersecurity.
With more attacks likely, the country should take advantage of its status as a newly-minted member of NATO to enlist outside expertise, say some.
“Montenegro is a NATO member, and we should seize the opportunity to invite experienced experts from NATO countries,” said veteran IT system engineer Ivan Bulatovic.
“They can help us make a plan, acquire the necessary equipment and train personnel to successfully deal with the cyber-attacks that await us in the future.”
Perpetrator still unknown
The attacks of August 22 last year compromised a string of public services, including the websites of the government and the Revenue and Customs Administration.
According to the Ministry of Public Administration, 17 “information systems” in 10 institutions were infected, with 150 computer directly affected.
Four days later, the National Security Agency told reporters that Russia was to blame, but offered no evidence. Then, Public Administration Marash Dukaj told Montenegro’s public broadcaster that it was in fact the work of a cybercriminal extortion group by the name of Cuba Ransomware.
“This group has created a special virus for this attack, a virus that cannot be created in a month, and perhaps not even in a year,” Dukaj said at the time. “These attacks were planned over a lengthy period of time; the very creation of the virus cost about $10 million and it has not been used anywhere so far.”
More than six months later, the National Security Council announced that, “given the specific nature and complexity” of the attack, it had been unable to determine exactly who was the perpetrator, despite the assistance of the FBI in the United States and the French National Cybersecurity Agency, ANSSI.
Bulatovic said the confusion only reinforced a perception that the authorities are at a loss to respond.
“It has not yet been announced what exactly happened, which systems were or are still compromised, how much and which data was lost, and what is the plan to prevent this or similar attacks in the future,” he said.
“The impression was that there was no plan of how to deal with such an attack, even though this type of incident is far from unusual in today’s world and happens on a daily basis.”
The Ministry of Public Administration rejected the criticism, telling BIRN: “We informed the public on several occasions that we had backup data from information systems and that the data was recovered through the restore procedure.”
Shortage of expertise
Experts say the mixed messages and lack of answers reflect serious shortcomings in Montenegro’s system of cybersecurity.
The Computer Incident Response Team, CIRT, a state cybersecurity team, has just seven employees, while nine officials work in the Directorate for System and Information and Communication Infrastructure. That’s the extent of Montenegro’s cybersecurity manpower when it comes to general defence of the public administration.
Dusan Polovic, director general of the Directorate for Infrastructure, Information Security, Digitisation and e-Services in the Ministry of Public Administration, conceded there were issues with the hiring and retention of staff, in particular because of the pay disparity between the public and private sectors.
Polovic said that a government decision to hike the basic pay of IT professionals in the public sector by 30 per cent had helped “to a certain degree”.
Even then, a typical salary for an IT professional on the public payroll rarely exceeds 1,000 euros per month, compared with a starting rate of 1,300 euros offered by private companies.
“Depending on one’s experience and seniority level, the salary can go all the way to 5,000 or even 6,000 euros per month,” said Danilo Nikovic, owner of the recruitment and human resources consultancy Millennial Consulting.
Most find work abroad or work online for foreign clients, he said. “This profession is in short supply everywhere in the world and therefore very well paid.”
Marko Lakic, an expert witness for the IT sector, said that Montenegro has cybersecurity experts, but only a handful work in state institutions.
“People who work as public officials cannot cope with digital security challenges,” Lakic told BIRN. “The state simply cannot pay experts as much as they can earn in the private sector.”
‘Basic’ digital maturity
Montenegro’s own Cybersecurity Strategy for the period 2018-2021 cites an “insufficiently developed awareness of the importance of investing in cybersecurity at the highest management levels.”
While many countries struggle with a lack of cybersecurity experts, the strategy states, the problem is more acute in Montenegro, which has a population of just 630,000 people.
Last year, a report by the European Bank for Reconstruction and Development, EBRD, characterised Montenegro’s level of “digital maturity” as “basic”.
It recommended adjusting educational curricula and introducing testing and certification of all civil servants using digital systems; the country should also introduce cybersecurity requirements for all digital service providers, not only in the public sector, it said, and ensure close coordination on security controls and practices.
Indeed, experience in the region shows that such attacks are only becoming more common and severe.
In September last year, just after the attacks on Montenegro, the Slovenian defence ministry and police were also targeted, though no critical systems were affected after authorities scrambled to contain the incident. The same month there was an attack on the state-level parliament and several other institutions in Bosnia and Herzegovina, rendering thousands of civil servants unable to carry their work.
Then in January, multiple institutions in Serbia came under cyber-attack, including domains under the jurisdiction of the main intelligence body, BIA. The hacker group Anonymous claimed responsibility.
Cybersecurity Ventures, one of the world’s leading publishers in the field, predicts the annual cost of global cybercrime will reach $10.5 trillion by 2025, up from $3 trillion in 2015.
Ban on browsing?
Eight months after the attacks in Montenegro, some digital services are still not functioning.
Polovic told BIRN that the only system under the Ministry of Public Administration that remains affected is the Open Data Portal, where public administration bodies can publish data in an open format.
But BIRN was unable to access a number of others, including Covid Odgovor.me, the Government’s website in charge of publishing the latest news on COVID-19 and Vertical and oblique ortho shots at the Ministry of Ecology, Spatial Planning and Urbanism.
According to the National Security Council, reports on the August 2022 attacks “contain a large amount of data important for the improvement of cybersecurity in Montenegro.” It did not specify who authored the reports, though the Council received input from the FBI, ANSSI and Montenegro’s own Council for Information Security.
The Ministry of Public Administration told BIRN that the reports were “classified in such a way that we do not have the authorisation to present their content, but that they can be used precisely for the purpose of improving security”.
The FBI declined to comment for this story, while ANSSI did not respond.
Bulatovic said that more attacks were “inevitable” and that Montenegro should look at bringing in private sector expertise, both local and international.
“They can train IT colleagues from the government and the ministries in how to apply the latest attack protection technologies,” he said.
“In addition, it is important to organise security training for all employees in the public administration, so that they can acquire basic knowledge about cybersecurity and use it in their daily work. For example, they must know how to recognise a fake email.”
Polovic said that that several such sessions had already been organised through the EU’s Cyber Rapid Response project for Montenegro, North Macedonia and Albania, with a focus on incident management and risk analysis.
He said that the Ministry of Public Administration had also launched multiple educational initiatives that will result “in the provision of expert training in this area.”
In March, the minister, Dukaj, said that the country would soon get a new addition to its cybersecurity infrastructure – the Agency for Cybersecurity. The agency should be founded once a new Law on Information Security is passed by parliament.
“This way, we establish a sustainable system for effective detection and defence against cyber threats and incidents of a high level of sophistication and ensure more efficient and safer functioning of the public administration and economy and contribute to public trust,” Maras said.
Lakic, however, identified a far simpler step – banning public servants and state officials from browsing web portals and watching YouTube content on state computers.
“Even with the existing infrastructure and employees – although I think they are not educated enough – it would greatly improve the security system,” he said. “We could solve over 80 per cent of threats just by making their behaviour more serious and responsible. We don’t even need money for this purpose, as we can do it without any additional investments.”
 Eurasia Press & News
Eurasia Press & News